
Knowledge Base
Identify Certificates Impacted by Potential Chrome Distrust
Browsers and root program owners have plans to remove trust of all legacy Symantec SSL/TLS certificates issued under the Symantec infrastructure. Websites and applications secured with these legacy Symantec SSL/TLS certificates trigger security warnings in browsers and applications relying on its root store:
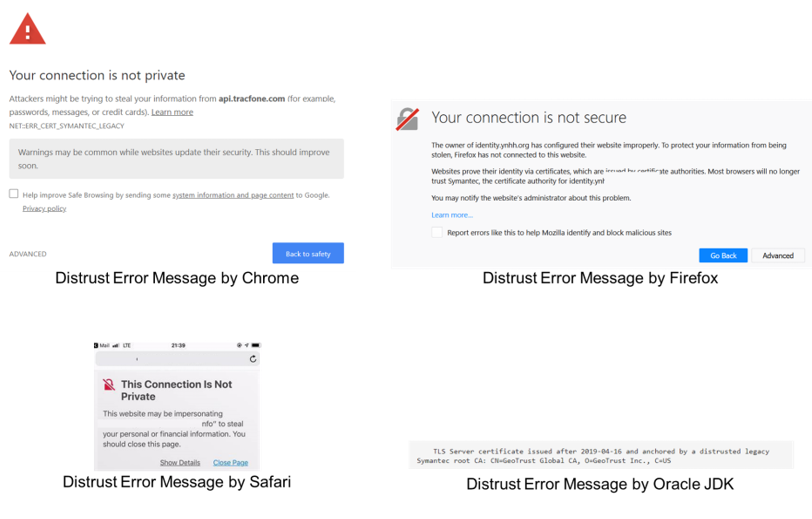
More details from Google, Mozilla, Apple, Microsoft, and Oracle:
Google security blog
- https://security.googleblog.com/2018/03/distrust-of-symantec-pki-immediate.html
- https://sites.google.com/a/chromium.org/dev/Home/chromium-security/symantec-legacy-pki
Mozilla security blog
- https://blog.mozilla.org/security/2018/03/12/distrust-symantec-tls-certificates
- https://blog.mozilla.org/security/2018/10/10/delaying-further-symantec-tls-certificate-distrust/
Apple information about distrusting Symantec certificate authorities
Microsoft partners with DigiCert to begin deprecating Symantec TLS certificates
Oracle's Plan for Distrusting Symantec TLS Certificates in the JDK
- https://blogs.oracle.com/java-platform-group/jdk-distrusting-symantec-tls-certificates
- https://java.com/en/jre-jdk-cryptoroadmap.html
DigiCert blog regarding Apple distrust
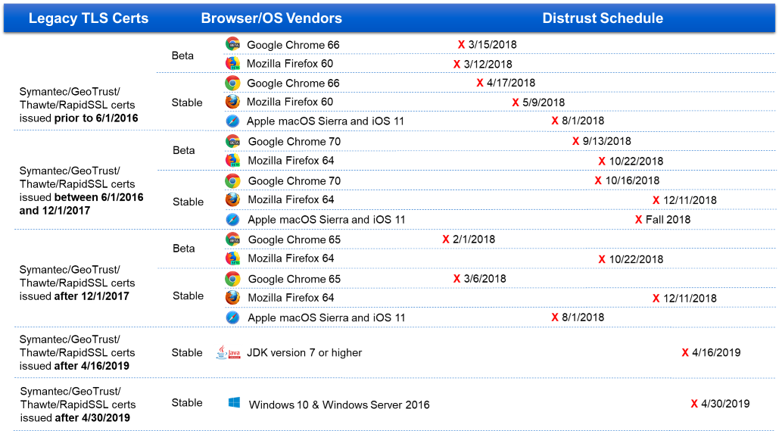
Symantec TLS/SSL certificates affected by distrust are based on their issuance date. Refer to this table and check your certificate inventory for certificates at risk of potential distrust.
Note:
- Final distrust of the Symantec SSL/TLS certificates in Chrome 70 stable will occur independent of Chrome release date.
https://sites.google.com/a/chromium.org/dev/Home/chromium-security/symantec-legacy-pki
Apple
- Apple distrust plan will affect not only browser but also applications you can download through the App store such as banking apps.
- Root update will be in effect for iOS 11 and Mac OS Sierra.
Oracle Java
- Starting on April 16, 2019, the JDK 7 or higher version will begin distrusting TLS Server certificates chaining to Symantec, Thawte and GeoTrust roots.
- Any TLS Server certificate issued on or before April 16, 2019 will continue to be trusted until it expires. Any certificate issued after that date will be rejected.
- Java Code Signing certificates chaining to Symantec and Thawte roots will not be distrusted.
- The restrictions will be enforced in the JDK implementation (the Sun JSSE Provider) of the Java Secure Socket Extension (JSSE) API. A TLS session will not be negotiated if the server's certificate chain is anchored by Symantec, Thawte and GeoTrust roots. An application will receive an Exception with a message indicating the trust anchor (root) is not trusted.
ex) TLS Server certificate issued after 2019-04-16 and anchored by a distrusted legacy Symantec root CA: CN=GeoTrust Global CA, O=GeoTrust, C=US
- If necessary, you can work around the restrictions by setting the jdk.security.distrustSymantecRoots system property to "false".
Enterprise customers
- Managed PKI for SSL and Complete Website Security (CWS) did not support no CT logging option between 6/1/2016 and 12/1/2017. All CT opt-out certs between them were logged with Root domain name.
Also distrusted - Certificates issued from the legacy Symantec root hierarchy on or after December 1, 2017
For uninterrupted business continuity, some Managed PKI for SSL customers continue to issue certificates from the legacy Symantec root hierarchy after the December 1, 2017 switch to the DigiCert hierarchy. These certificates are already distrusted by Google Chrome and will be distrusted by Apple on August 1, 2018.

