Knowledge Base
Keygen support dropped with Firefox 69 | PKI Platform
What is Keygen?
The HTML <keygen> element exists to facilitate generation of key material, and submission of the public key as part of an HTML form.
This mechanism is designed for use with Web-based certificate management systems.
It is expected that the <keygen> element will be used in an HTML form along with other information needed to construct a certificate request, and that the result of the process will be a signed certificate.
What is happening?
The support for the non-standard <keygen> HTML element and HTMLKeygenElement DOM interface has been removed with Firefox 69.
How does this work?
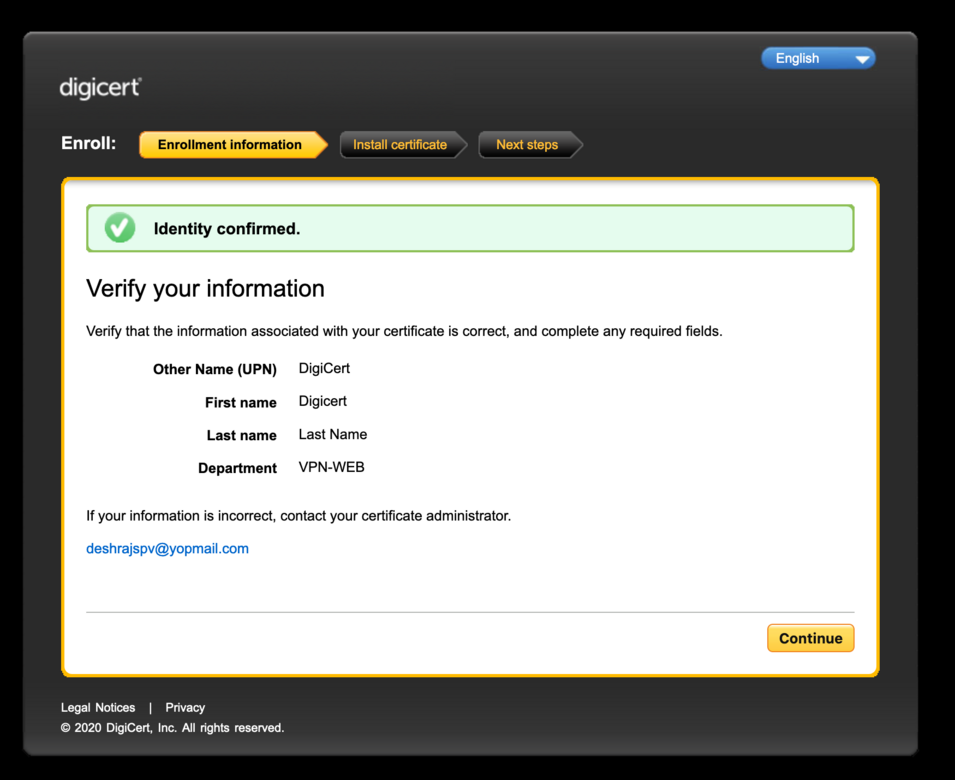
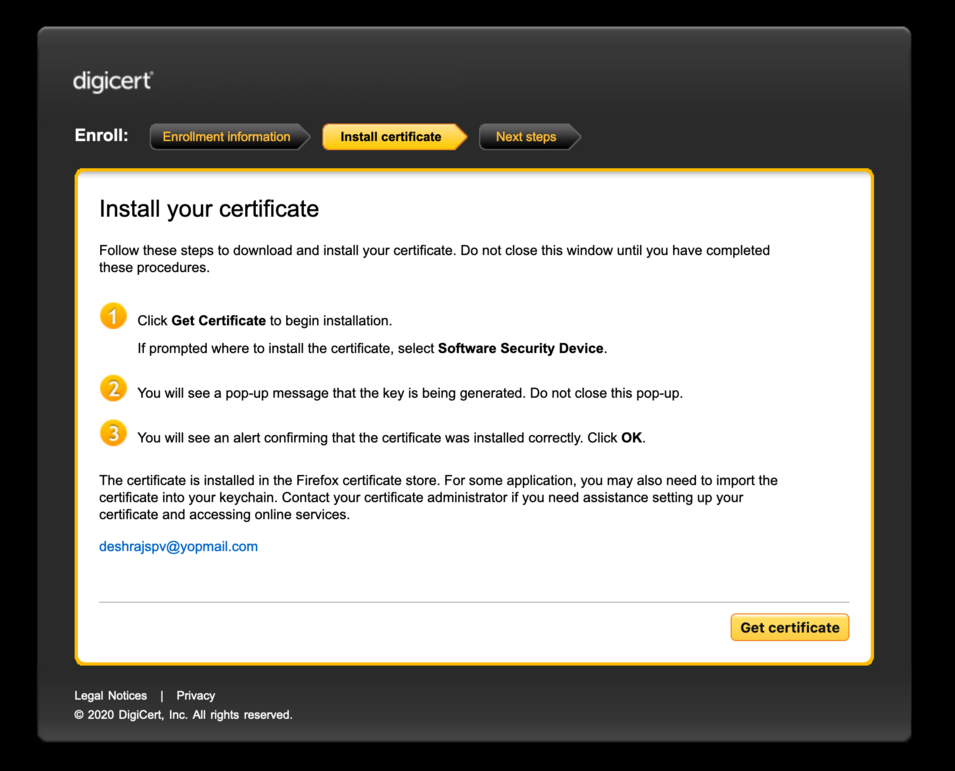
Once a user has been authenticated, we will be generating the key pair / CSR in memory and submit it for signing. Once we receive the cert, we will package it up with the matching private key as a password protected PKCS12 file and show it in a webpage for the user to download and install.
Once the p12 file is available on the page, we would destroy all key material and cert so, the user only has 1 shot at downloading the cert. If they do not, they will have to re-enroll for the cert.
Note: There is no action required on your current certificate. You can use it until expiry.
What Browsers support Keygen?
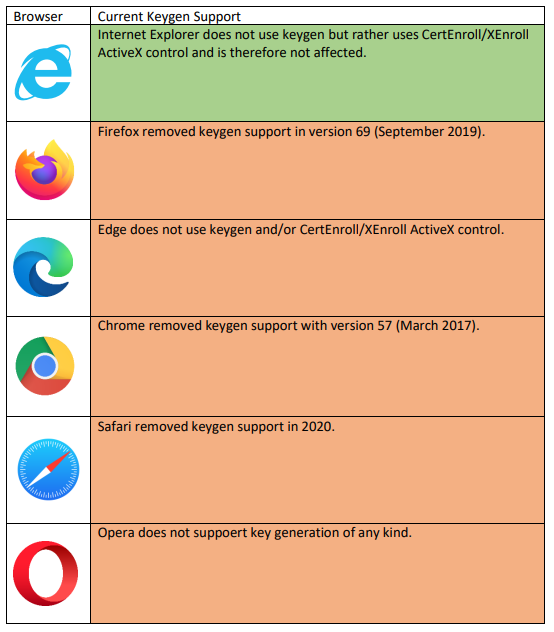
What has changed from 8.19.6 release onwards?
Firefox 69 and above for both Windows and MacOS will work fine for certificate issuance. It will deliver a password-protected certificate in PKCS12 format that can be downloaded and manually installed on Firefox, or any browser/platform that has browser caching enabled.
What are supported?
- SMIME
- Client Certs
- Code Signing
- Admin IDs
Certificate issuance via Cloud Self-service portal, Enterprise Gateway use cases and normal user flows are supported.
What happens now?
When picking up a certificate:
- A Key Pair and CSR(SPKAC) will be generated.
- The Private Key will be stored in Session Storage with encryption.
- The CSR will be sent to server.
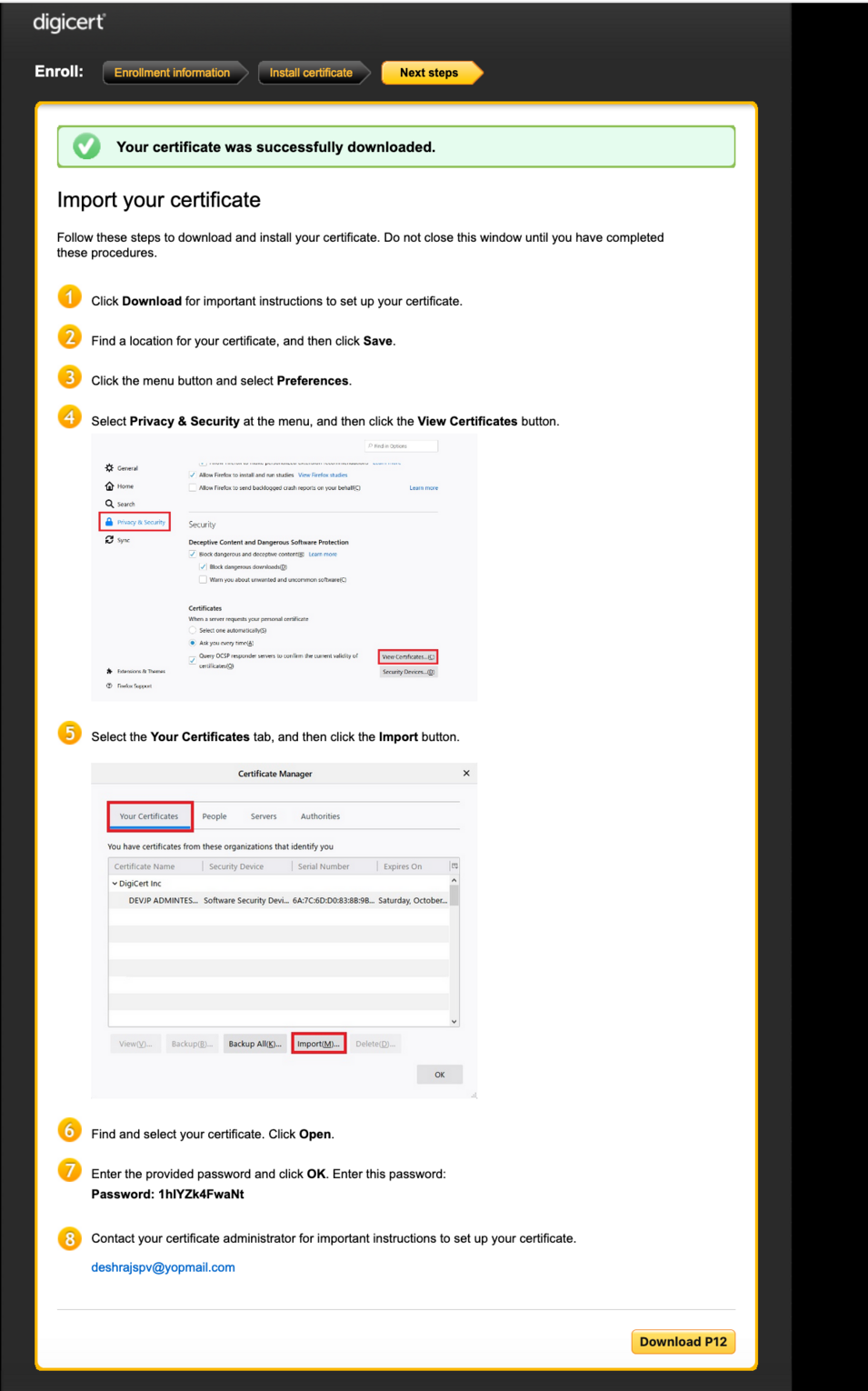
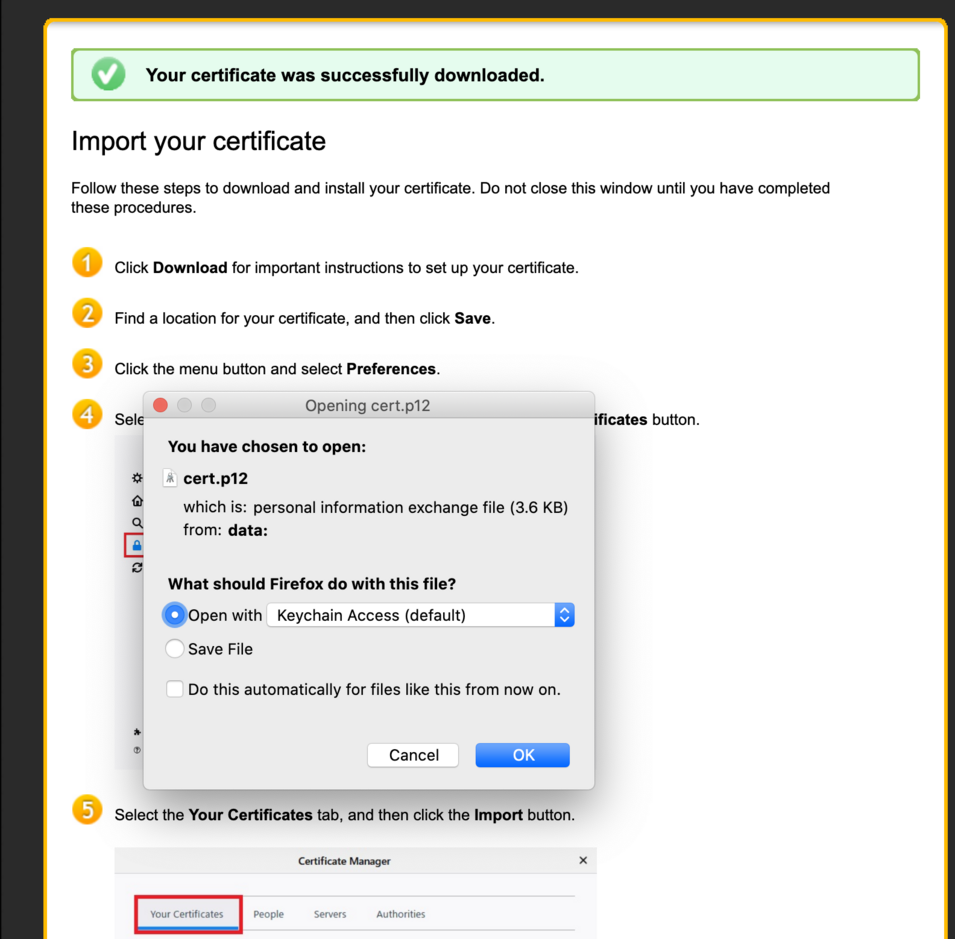
When downloading the certificate:
- The issued certificate (PKCS#7) will be downloaded.
- The certificate will convert to PKCS#12.
- The password of P12 will be generated.
Pre-requisite for Firefox:
Before you start to issue a certificate, please confirm the use of “Web (Session) Storage” in Firefox. To verify this, follow these instructions:
- Type ‘about:config’ in the address bar
- You may need to click ‘Accept the risk and continue’ button
- Type ‘dom.storage.enabled’ and set ‘true’
For example, a normal user client authentication certificate issuance from Firefox 72 browser: