
Knowledge Base
How to Enable Real-time Traffic Anomaly Detection
DNS Made Easy's Real-Time Traffic Anomaly Detection (RTTAD) is our proprietary machine-learning tool that proactively monitors your domain's unique traffic patterns. When there is an unexpected spike in traffic or suspicious activity is detected, RTTAD sends an instant alert to IT teams. The collected data can be repurposed to best suit the organization's needs. This guide will walk you through the process of enabling RTTAD for a domain(s) in your DNS Made Easy account.
Common Use Cases for Real-Time Traffic Anomaly Detection
This service work with DNS Made Easy’s analytics tools to monitor DNS traffic in real-time and is most commonly used to assist in detecting:
- Distributed-denial-of-service (DDoS) attacks
- System configuration trouble
- System outages
- Firewall configuration issues
- Marketing issues
Prerequisites
- A domain has been added to your DNS Made Easy account
- Basic understanding of DNS Analytics
- You have purchased the necessary amount of query logging events needed for your domain(s)
Note: To increase your query quota for Real-time Traffic Anomaly Detection, click the orange Increase Quota button on the main Analytics dashboard page.
How to Enable Real-Time Traffic Anomaly Detection
1. Navigate to the RTTAD Portal
Once logged into the DNS Made Easy dashboard, click the option for Query Logging from the left-hand menu to access the Analytics platform.

At the login prompt, enter your username and password.

2. Navigate to the RTTAD Portal
Once logged in to Analytics, click on any of the + icons under the Anomaly column to enter the RTTAD portal.
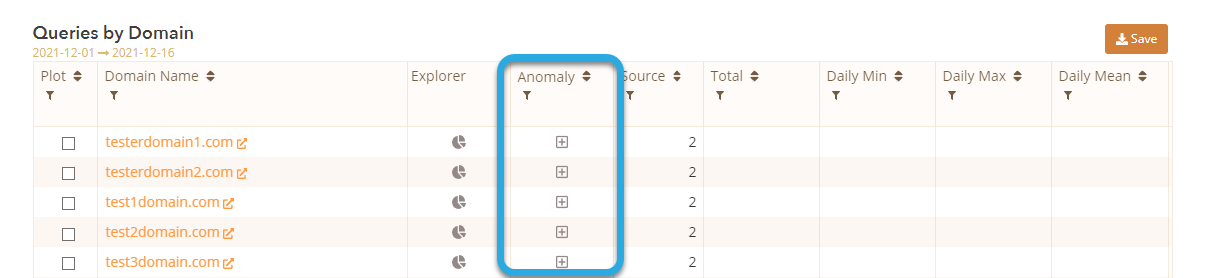
3. Select the Domain(s) That Needs RTTAD Enabled and Configure
You should now be in the Anomaly Detection portal. In the Manage Scheduled Anomaly Detections section, check the box next to the domain(s) you want to enable RTTAD for, and then click on Aggregated to World to expand the menu options for your aggregation preference.
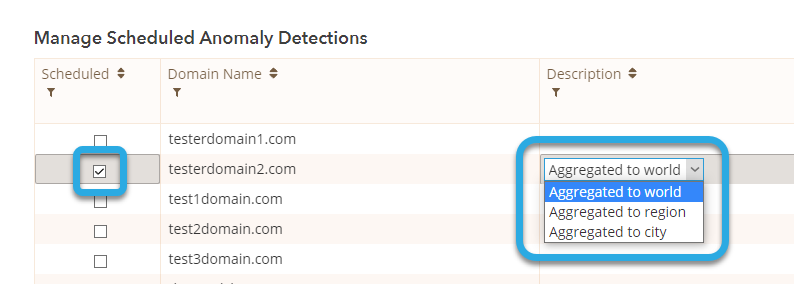
- Aggregated to the world - this selection bases the anomalies on the sum of the domain's traffic from around the world. This option is recommended for domains that receive five billion or below queries per month.
- Aggregated to the region - this selection bases the anomalies on the sum of the domain's traffic for a specific region. This option is recommended for domains that receive above five billion
- Aggregated to the city - this selection bases the anomalies on the sum of the domain's traffic for a specific city, which gathers information from each point of presence (PoP) from around the world.
After selecting the aggregate option you want to use for your domain, click Save in the right-hand column.
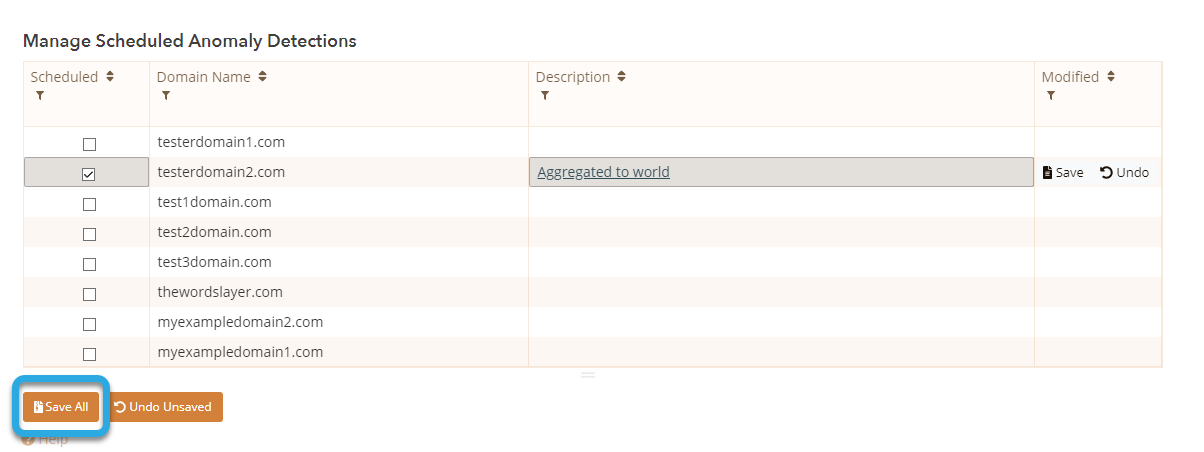
4. Save Configuration(s)
To complete your RTTAD configuration(s), click the Save All button on the left. RTTAD is now enabled for the selected domain(s).
In order to receive instant notifications about your domain activity, you will need to set up notification groups. See our Create Contact Group tutorial if you need help with this step.
Anomaly Detection Notifications
Once notification groups are established, each contact in the group will receive an instant email notification any time an anomaly is detected. The email will entail any relative information, including a graph of any traffic dips or spikes that triggered the notification.
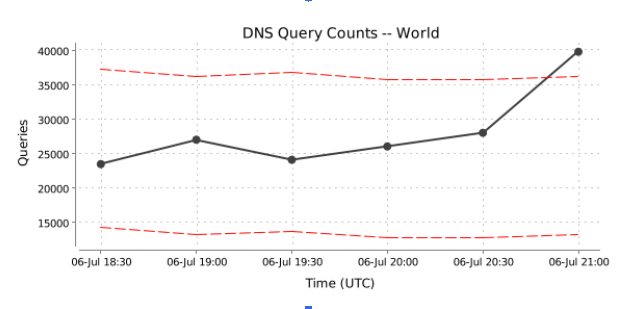
This data can be used to investigate where traffic is coming from (region, record name, etc.) via the Data Explorer. IT teams can use this information to determine if the activity is legitimate or malicious and take action accordingly.
Visit our website for more information on our features and services.

