
Knowledge Base
CAA Records
Certification Authority Authorization (CAA) records allow a domain name holder to specify one or more Certification Authorities (CAs) authorized to issue certificates for that domain. (RFC 6844)
- CAA records are intended to prevent CAs from improperly issuing certificates.
- CAA records can set policy for the entire domain, or for specific hostnames.
- CAA records are also inherited by subdomains, therefore a CAA record set on example.com will also apply to any subdomain, such as subdomain.example.com (unless overridden).
- CAA records can control the issuance of single-name certificates, wildcard certificates, or both.
1. Navigate to Managed DNS

2. Select your Domain

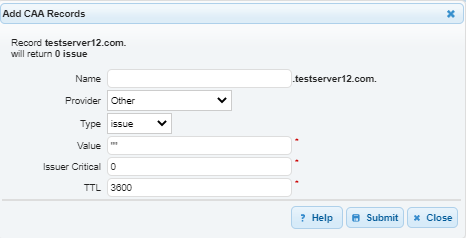
3. Add the CAA Record
Under CAA Records click the plus sign to add a new record.

4. Enter CAA Record values
- Enter a name for the record.
- In the drop-down menu choose your CA (certificate authority) provider. The hostname of your provider will automatically populate the Value box.
If your provider is not listed, then choose another, and enter the hostname of the provider in the Value box. - The Type dropdown menu allows you to choose how you want certificates to be issued by the CA. Each CAA record can contain only one tag-value pair. For information on the types of tags, please refer to the Configuration section.
- In the Issuer, the Critical box enters either a 1 or a 0. The default setting is 0, which is for “not critical”. Currently, CA’s do not recognize any value other than 0.
- You can edit the default TTL if needed.
- Click Submit.
Configuration
Flag
All records will have the default issuer critical value of 0, which means they are “not critical”. At this time, CA’s do not recognize any other flag values.
Type (Tag)
Type allows you to choose how you want certificates to be issued by the CA. Each CAA record can contain only one tag-value pair.
Options:
- issue: Explicitly authorizes a single certificate authority to issue a certificate (any type) for the hostname.
- issuewild: Authorization to issue certificates that specify a wildcard domain.
Please note: issuewild properties take precedence over issue properties when specified. - iodef: (Incident Description Exchange Format) Specifies a means of reporting certificate issue requests or cases of certificate issue for the corresponding domain that violate the security policy of the issuer or the domain name holder.
The Provider (Value)
Specify the domain name of the CA provider to which the CAA record applies. The Value field will automatically populate with the FQDN of the CA provider. If your CA is not in this list, select Other and enter the domain name in the Value box.
The <character-string> encoding of the value field is specified in [RFC1035], Section 5.1.
Canonical Format
When you are configuring CAA records you will need to present the record values in the following format:
<flags> <tag> <value>
example.com. CAA 0 issue “ssl.com”
Use Cases
Let’s create a CAA record for a domain that authorizes certificates to be issued by Comodo and SSL.
example.com. CAA 0 issue “comodo.com”
example.com CAA 0 issue “ssl.com”
If Comodo does not understand the record information, it will not return a certification. Instead, SSL will respond.
Now, what if we wanted to issue a wild card for SSL? We would change the type value to issuewild.
example.com. CAA 0 issue “comodo.com”
example.com CAA 0 issuewild “ssl.com”
Since wild cards take precedence, Comodo will not be able to issue a wild card certificate.
If you want to receive policy violations from CAs, you can change the type to iodef and replace the provider value with your contact email preceded by mailto:
example.com. CAA 0 iodef “mailto:admin@example.com”

