
Knowledge Base
DigiCert AutoEnrollment Server: Support for EOBO (Enroll On Behalf Of)
Description
1. What is EOBO?
This feature builds on the autoenrollment use case by introducing a co-signer for the certificate request. In this use case, the enrollment agent creates and signs the initial certificate request. The enrollment agent then submits the signed request to the CA. The CA returns the issued certificate to the enrollment agent, who then provides the issued certificate to the end entity via an out-of-band process.
For more information, refer to the Microsoft documentation.
2. How to setup and enroll with EOBO
a. Prepare the Enrollment Agent certificate template
- In PKI Manager, create a profile using the Microsoft Enrollment Agent enrollment method.
- Download the AE-Config file and import it to the Autoenrollment Server machine using the Autoenrollment Server configuration utility.
- Refer to the Autoenrollment Server deployment guide section About the Assignment of Group/User Access to Templates.
- Log into Windows as the Authorised user (Administrator) to issue the Enrollment Agent certificate.
- Using MMC (Microsoft Management Console), add the Certificates snap-in, then right click Certificates under Current User, and select Request New Certificate:
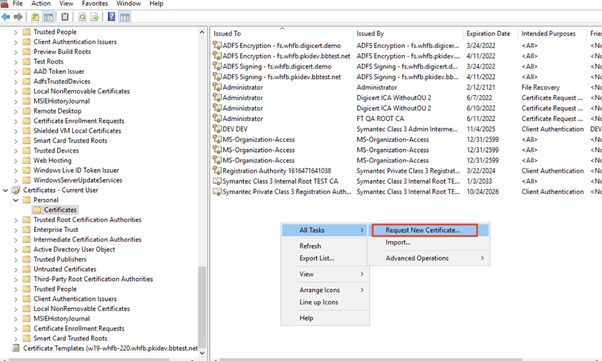
Follow the wizard prompts to issue the Enrollment Agent certificate.
b. Prepare the template to issue certificates using EOBO
- Choose the template to issue certificates using EOBO.
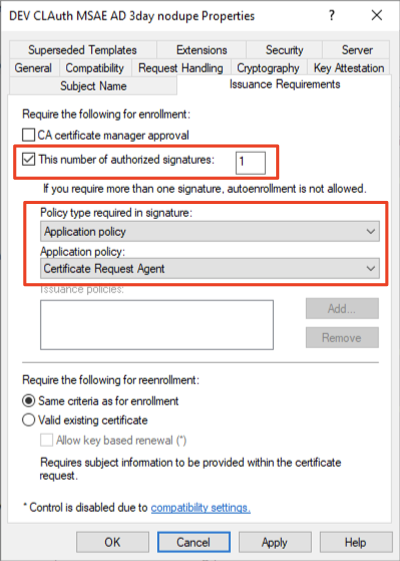
- Under the Issuance Requirements tab, select the following:
- Check This number of authorized signatures, and specify the number of signatures required.
- For Policy type required in signature: select Application policy.
- In the Application policy dropdown, select Certificate Request Agent.
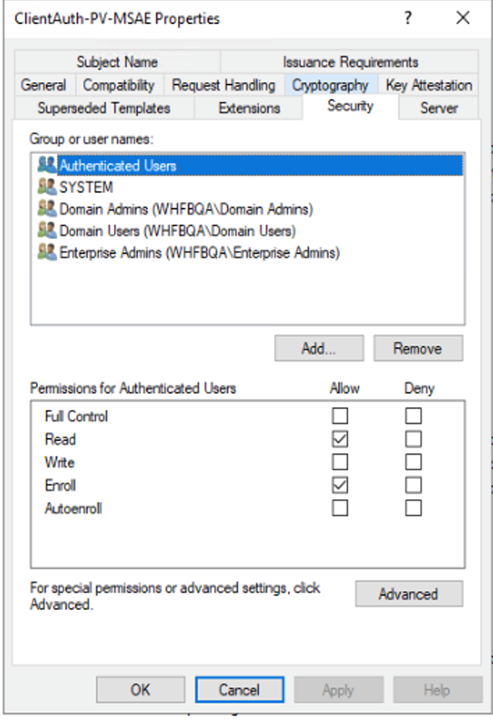
- Under the Security tab, do not select the Autoenroll permission– autoenrollment functionality is not supported for EOBO.
- Select Allow for Enroll for that user/group for whom you intend to issue certificates using the EOBO feature.
c. Enrollment Agent user action
- Log into Windows as the Authorised user (Administrator) who has a valid Enrollment Agent certificate installed.
- Using MMC, right click Certificates under Current User, and select Enroll On Behalf Of…
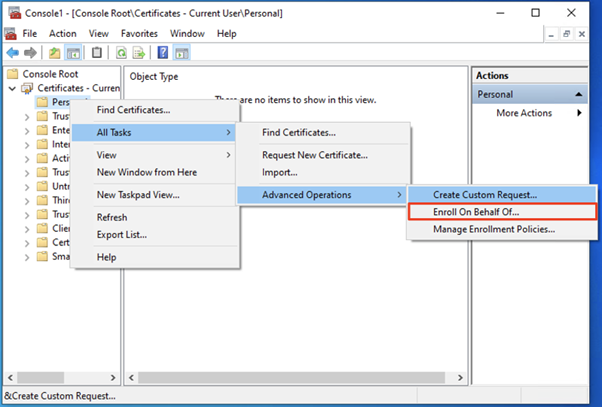
- In the enrollment wizard, follow the prompts until the following dialog is shown:
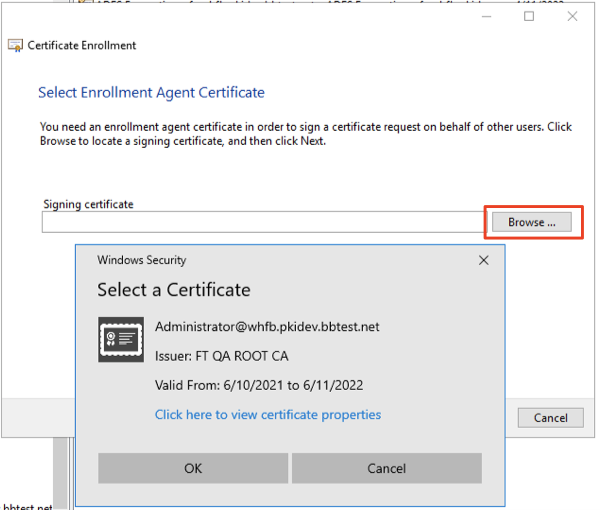
- Select Browse. An Enrollment Agent certificate should be shown.
Note: If no certificates are shown, there may be an issue with the CRL of the certificate or with the CA certificates in the chain. See the Troubleshooting section below to aid in diagnosing the issue. - Select Next, then select the template:
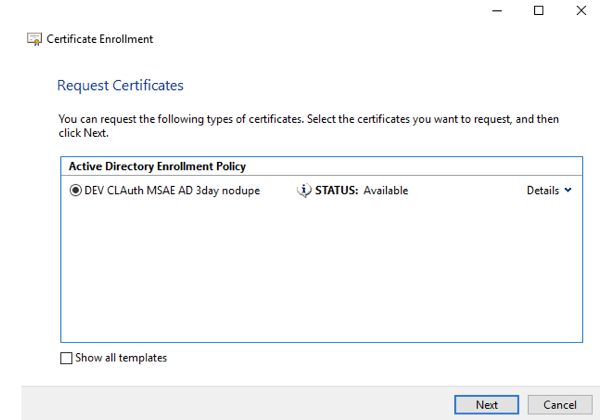
- Select Next, then enter the user name or alias for whom the certificate is being issued:
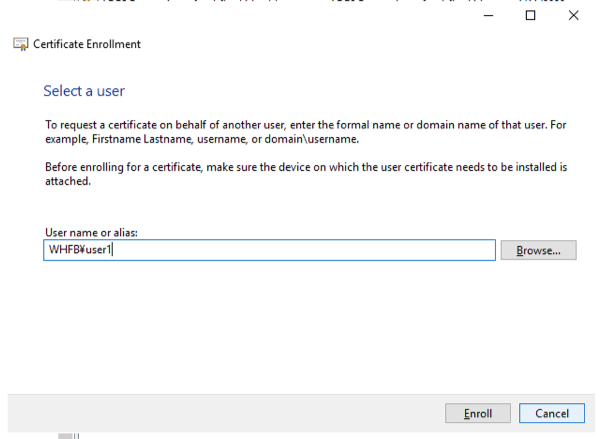
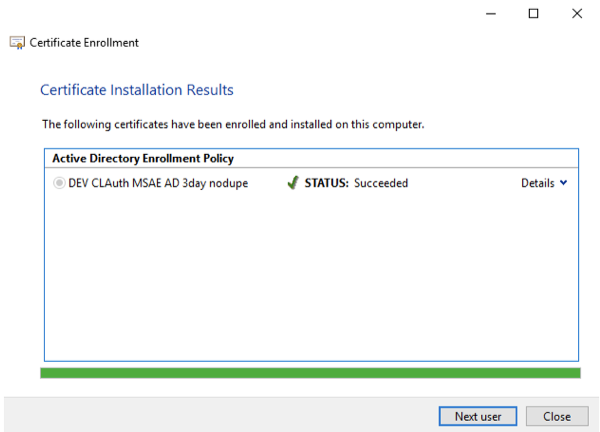
- Select Enroll. The screen below will show in the event of a successful enrollment:
d. Renew certificates issued by EOBO
There are four methods to renew an EOBO-issued certificate:
- Re-enroll: Similar to the initial enrollment, an Enrollment Agent certificate signature is required. The certificate can be requested with the same key as the original, or with a new key.
- Renew: Certificate request is signed by the existing key (proof of possession renewal). The certificate can be requested with the same key as the original, or with a new key.
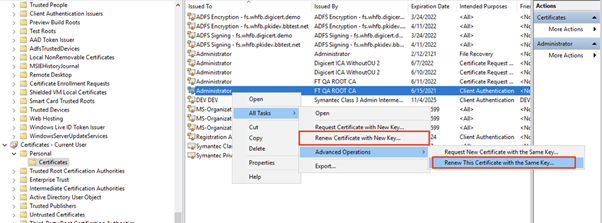
- The distinction between Re-enroll and Renew is whether or not the profile is allowed to Renew without Enrollment Agent signature, using POP (proof of possession) of the current certificate.
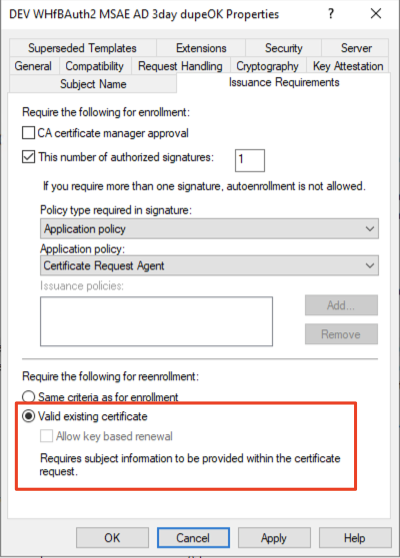
- This is configured in the certificate template using the Valid existing certificate radio button under the Issuance Requirements tab:
Troubleshooting
If there is no certificate that meets the criteria for the Enrollment Agent Certificate, the Confirm Certificate dialog will show No certificate available:
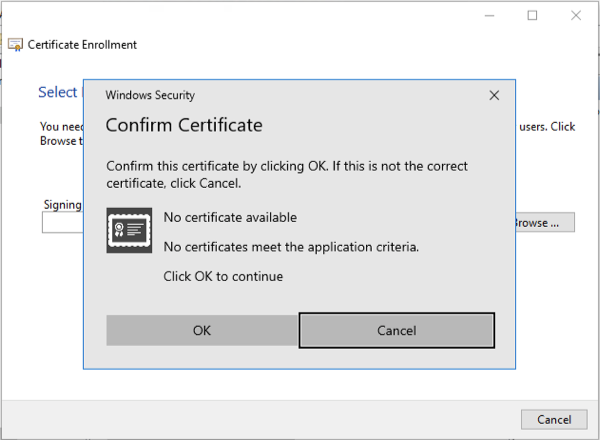
The following criteria apply:
- The certificate needs to be issued using the Microsoft Enrollment Agent template, particularly the EKU (Extended Key Usage) 1.3.6.1.4.1.311.20.2.1 is required.
- The CA certificate chain needs to be trusted on the device where the certificate is being installed.
- The certificate must pass a revocation check:
- Both the end entity and intermediate CA certificates must pass the revocation check
- Both the end entity and intermediate CA certificates require working CRL or OCSP
For point 3 above, the revocation checks for the certificates can be verified using the following command:
- certutil -urlfetch -verify <x509 enrollment agent cert>
The CRL information cache can be cleared and refreshed using the following commands:
- certutil -urlcache crl delete
- certutil -setreg chain\ChainCacheResyncFiletime @now

