
Knowledge Base
Enrollment over Secure Transport (EST) | PKI Platform
The Enrollment over Secure Transport (EST) is a protocol used to securely provision RSA or ECC certificates over HTTPS, as described in RFC 7030. EST uses HTTPS as a transport protocol and leverages TLS ciphers to establish a secure TLS channel from an EST client to the EST server, used to send EST operations.
The device requesting the certificate is known as the EST client. The client communicates with an EST server, which authenticates/authorizes requests from clients before issuing a certificate from a configured Certificate Authority (CA).
The DigiCert EST service implements the below operations:
- cacerts – to download the CA certificate bound to a certificate profile
- simpleenroll – to enroll for a certificate
- simplereenroll – to renew a certificate
Authentication Methods
The DigiCert PKI Platform supports the following methods, in order to authenticate/authorize a request for a certificate over EST:
- TLS Client Authentication (known as Certificate Authentication), supporting the following use-cases:
- Using a client certificate issued by a CA within the customer's DigiCert PKI Platform account.
- Using a previously installed certificate (e.g. a manufacturer certificate or a certificate issued by some third party), which has been provisioned to the devices prior to enrolling for its own device authentication certificate via EST.
- Using an RA certificate that acts as a central EST proxy server that communicates with the DigiCert PKI Platform EST service on behalf of clients. You can enroll and download an RA certificate from the PKI Manager portal.
When using TLS Client Authentication, the Issuing CA must be configured with the DigiCert PKI Platform account as a pre-requisite – see the “Configuring EST authentication and valid client IP addresses” section for details.
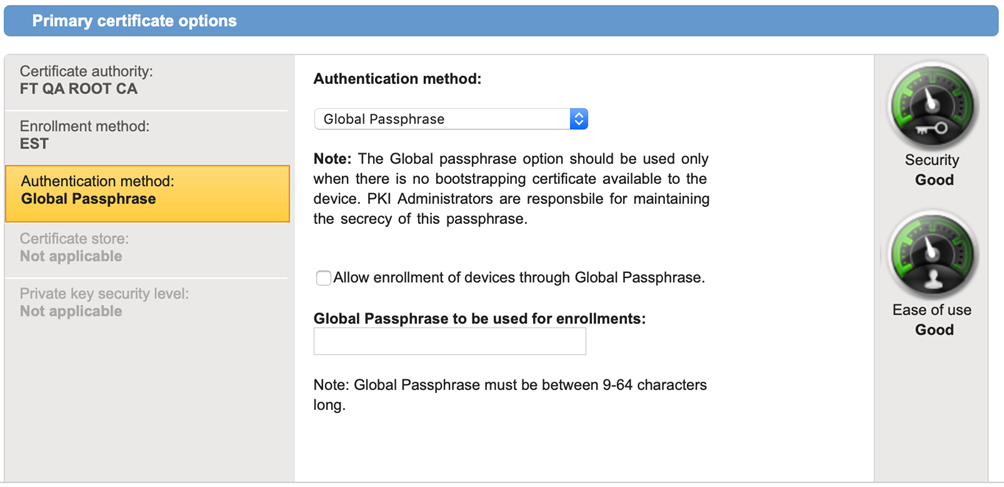
- Global Passphrase (Pre-shared Secret)
- Used to authenticate all devices using a shared global passphrase, when devices have not been bootstrapped using a digital certificate. The global passphrase is established by the administrator of a DigiCert PKI Platform account against a certificate profile.
- Used to authenticate all devices using a shared global passphrase, when devices have not been bootstrapped using a digital certificate. The global passphrase is established by the administrator of a DigiCert PKI Platform account against a certificate profile.
Configuring a Certificate Profile for EST
Pre-requisite: User must have admin rights to create and manage certificate profiles.
To configure a certificate profile for EST, follow the below steps:
- Access the DigiCert PKI Manager and select one of the following templates to create a certificate profile:
- Client Authentication
- Generic Device Authentication
- Select the CA certificate used to issue your certificate. The DigiCert PKI Platform supports both RSA and ECC CAs, but they need to be created and loaded onto your account before appearing on the Certificate Authority drop-down list. Contact your DigiCert representative for assistance.
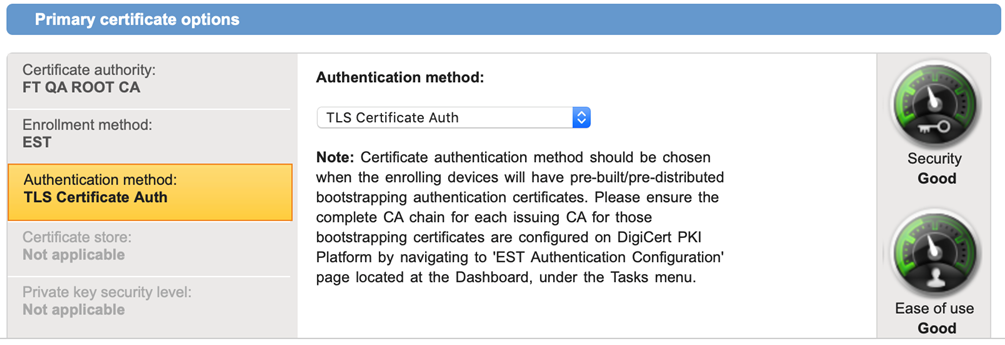
- Under Primary certificate options, select EST as an Enrollment Method from the drop-down list.
- Select one of the following Authentication Method from the drop-down list:
- TLS Certificate Auth
- Global Passphrase
- Configure the rest of the certificate profile options to meet your certificate requirements, e.g. Subject DN, Subject Alternative Names, Key Usage, Extended Key Usage, signing algorithm, validity periods, etc.
- Save the profile. This will generate a unique EST responder URL that can be used to configure EST clients. Here’s an example EST URL for the Production platform:
https://pki-est.symauth.com/.well-known/est/<profile-oid>
Proceed with configuring the EST authentication and client IP addresses below
Configuring EST authentication and valid client IP addresses
When configuring the TLS Client Authentication method, the EST client uses a certificate (typically a Bootstrap/Manufacturing CA, or even an EST Proxy CA certificate), which must be configured as a trust anchor within the DigiCert PKI Platform to authenticate incoming EST requests. This is achieved by following the below steps:
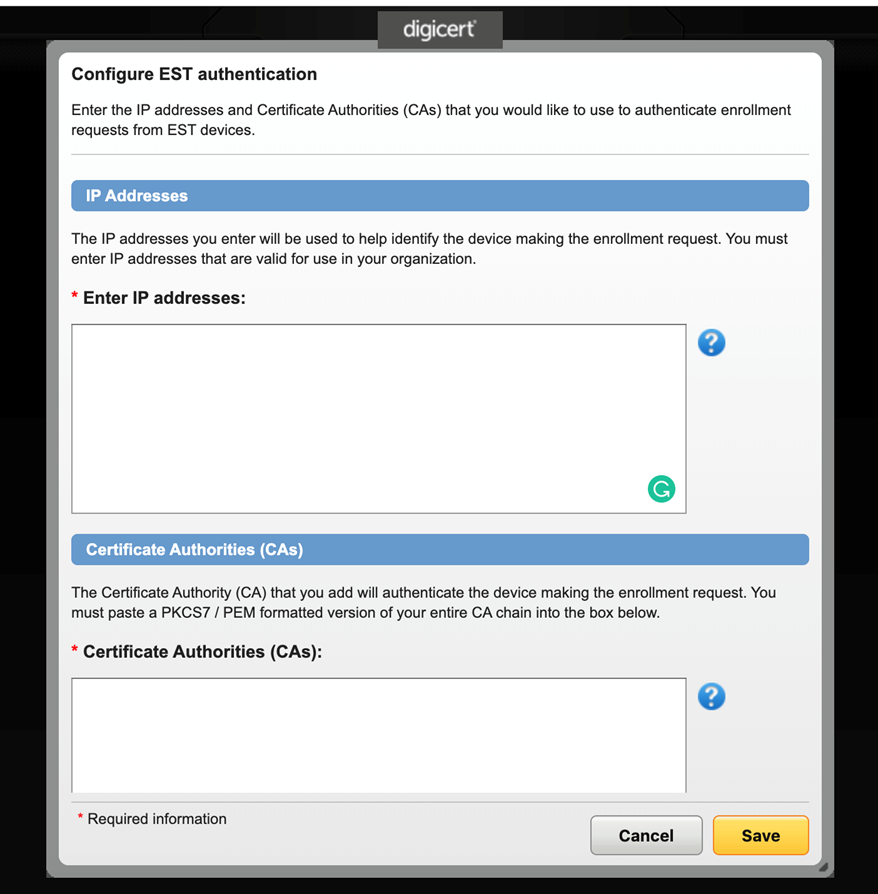
- Access the DigiCert PKI Manager, click on Tasks and select EST Authentication.
- Paste the Issuing CA (or CAs) which are used to authenticate incoming EST client requests into the Certificate Authorities (CAs) text field. Typically, this CA is used for bootstrapping purposes, and used to issue the final certificate via EST, then used to authenticate to the target service. However, once the Client Authentication certificate is provisioned to the device, this new Issuing CA will be used to authenticate subsequent renewal certificate requests. Therefore, the Issuing CA also needs to be whitelisted/uploaded onto the EST Authentication page – Certificate Authorities (CAs) text field.
All Issuing CAs must be uploaded as separate PEM-formatted PKCS7 text objects onto the same Certificate Authorities (CAs) text field.
Note: when using the Global Passphrase authentication method, a dummy CA will need to be entered, even though not used as part of the authentication method. This issue will be resolved in the next release of the product.
To provide additional security to incoming EST client requests, the DigiCert PKI Platform service requires PKI administrators to configure/whitelist the IP addresses from which EST client requests originate from, by entering IP v4 addresses within the provided text field. This can be the source IP addresses for the end-devices, or the IP address of an EST proxy server. You can configure a subnet of IP addresses, e.g. 143.11.129.0/255, which will whitelist all IP addresses from 143.11.129.0 to 143.11.129.255
This is currently a mandatory security feature, regardless of the Authentication Method being configured for the certificate profile.
Requesting and Issuing a Certificate via EST
To request and issue a certificate using the DigiCert PKI platform via EST, perform the following steps, for which it is assumed that the EST client has been configured with the EST Server URL created as part of the certificate profile creation process.
- Client generates key pair and Certificate Signing Request (CSR).
- Client submits ‘simpleenroll’ request using the pre-configured EST Server URL.
- DigiCert EST Server authenticates the incoming request using the designated Authentication Method configured in the certificate profile (TLS Client Auth or Global Passphrase).
- If TLS Client Authentication is used, the signed incoming request is checked against the configured CA and list of whitelisted IP addresses.
- If Global Passphrase is used, the EST request must contain the same passphrase as configured by the PKI administrator.
- If all authentication steps are satisfied, a certificate is issued to the EST client, signed by the configured CA within the certificate profile.
Renewing a Certificate via EST
To renew a certificate, the EST client must submit a ‘simplereenroll’ request and establish a TLS authenticated channel making use of the existing certificate, thus using proof of possession-of-private key. You must ensure the CA used to issue the client authentication certificate to the devices is whitelisted within the EST Authentication page in PKI Manager – see Configuring EST authentication and valid client IP addresses section above for details.
Note that the IP address of the incoming renewal request will continue to be checked by the DigiCert EST service, and only issue a renewed certificate if:
- the client source IP address is allowlist
- the certificate being renewal is not revoked, i.e. is valid, or expired
- the renewal request is within the renewal window configured within the certificate profile

