
Knowledge Base
Sign Java .jar files with a hardware token-based code signing certificate in Windows
Signing Java .jar Files with the CLI (Command Line Interface) Command Jarsigner
These instructions are for signing Java .jar files with a code signing or EV code signing installed on a hardware token.
When you use your certificate to sign code, a digital signature is applied to your code. This digital signature boosts customer confidence in the code they are about to download and helps to improve the adoption of your Java applications. Many end-users cancel downloads or installations when they receive a warning that an unknown publisher signed the code.
Sign .jar Files using the CLI Command Jarsigner
- Create a file named eToken.cfg that contains the following lines, and save it to your JDK bin folder (C:\Program Files (x86)\Java\jdk1.7.0_05\bin).
name=eToken
library=c:\WINDOWS\system32\eTPKCS11.dll
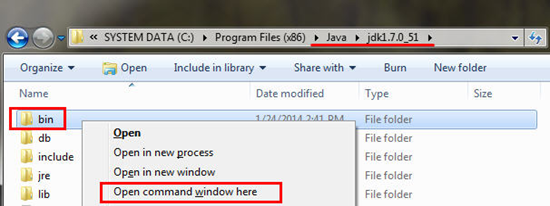
- In Windows Explorer, navigate to the JDK folder.
- In the JDK folder, push and hold Shift, right-click on the bin folder, and select Open command window here.
- To view your code signing or EV code signing certificate and the certificate alias on the token:
- Plug in your token.
- Run the following command from the command prompt:
- Sample output:
In this example, 7800FA4C81523ACA is the certificate alias you use to sign .jar files.
Keystore type: PKCS11
Keystore provider: SunPKCS11-eToken
Your keystore contains 1 entry
7800FA4C81523ACA, PrivateKeyEntry,
Certificate fingerprint (SHA2):
XX:XX:XX:XX:XX:XX:XX:XX:XX:XX:XX:XX:XX:XX:XX:XX:XX:XX:XX:XX
Keytool -list -keystore NONE -storetype PKCS11 -providerclass
sun.security.pkcs11.SunPKCS11 -providerArg ./eToken.cfg
enter keystore password: [enter password]
Note: with newer versions of SafeNet Authentication Client (SAC) driver the “Certificate Alias Value” is going to be the organization name.
Here is sample output from a Code Signing token using the newer SAC drivers (sceenshot 1):

Solution:
The “Certificate Alias Value” may not be a random string of alpha-numerical characters. It may be that it is the organization name as listed in the Keytool command output. It will be the string prior to the comma of “PrivateKeyEntry”. In our case it is “Win the Customer, LLC” instead of a random value.
ALTERNATIVE SOLUTIONS:
It is totally possible that there is no value associated with the certificate alias: organization name or otherwise. In this case the customer should try running the Keytool command on a different network/machine because there could be group policy settings or something that is prohibiting Keytool from communicating with the token and accessing the value necessary for signing.
If the incorrect Certificate alias is specified you will the following error message: java.security.KeyStoreException: PKCS11 not found.
To fix the above error you need to add slot=0 and to find the correct slot used by the token, please set the slot number to zero in your eToken.cfg file (slot=0).
Attempt to run the list command again, incrementing the slot number by 1 with each iteration of the error.
You should eventually receive the Enter KeyStore Password prompt that will accept your SafeNet Token passphrase.
etoken.cfg:
”name=eToken
library=c:\WINDOWS\system32\eTPKCS11.dll
slot=0”
5. To use the code signing certificate on the token to sign file.jar, run the following command from the command prompt:
jarsigner -tsa http://timestamp.digicert.com -verbose -keystore NONE -
storetype PKCS11 -providerClass sun.security.pkcs11.SunPKCS11 -
providerArg ./eToken.cfg "C:\path\to\file.jar" "7800FA4C81523ACA"6. If the command executed successfully, you should see something similar to the following sample output:
Enter Passphrase for keystore:
adding: META-INF/7800FA4C.SF
requesting a signature timestamp
TSA location: http://timestamp.digicert.com
adding: META-INF/7800FA4C.RSA
signing: DigiCertTest.class
jar signed.
Troubleshooting
- The program pauses and does not prompt you to enter your password.
If you run the keytool or jarsigner command and the program pauses and does not prompt you for a password, unplug the device (token) and plug it back in. Run the command again. This time it should work.
- "jarsigner error: java.lang.ClassNotFoundException: sun.security.pkcs11.SunPKCS11"
This error occurs when using a 64-bit version of the JDK. To eliminate this error, download and use a 32-bit version of the JDK.
- "jarsigner error: java.lang.RuntimeException: keystore load: load failed"
This error may occur if you enter the wrong password.
- "keytool error: java.security.KeyStoreException: PKCS11 not found"
This error occurs if your config file fails to load correctly or the config file points to a file that does not exist (e.g., library=c:\WINDOWS\system32\eTPKCS11.dll).
Another solution would be adding the following line to the eToken.cfg "Slot=0"
To identify the correct slot number, set the slot number to zero and attempt to run the sign command again, incrementing the slot number by 1 with each iteration of the error.
This error sometimes indicates that the token's device drivers are not installed on your computer. For more information about installing the drivers, see the following knowledge base articles:

