
Knowledge Base
DigiCert Validating DNSSEC when Verifying Domain Control and Performing CAA Checks
| Important: This is a dynamic article. DigiCert may update this article if new information becomes available. Save this page and check for updates. The Last Modified date appears under the title of the article. |
| New date - March 3, 2026 DigiCert will start validating DNSSEC when verifying domain control and performing CAA checks on March 3. The new date gives you an extra week to prepare. See Verify DNSSEC configurations before March 3, 2026 below. |
Description
On March 3, 2026, DigiCert will start validating Domain Name System Security Extensions (DNSSEC), if present, during domain control validation and DNS Certification Authority Authorization (CAA) checks. This change affects all products that require domain validation and/or CAA checks before certificate issuance:
- Public TLS certificates (DV, OV, and EV)
- X9 PKI for TLS certificate
- EU Qualified Website Authentication Certificate (QWAC)
- EU Qualified Website Authentication Certificate PSD2
- PKIoverheid Private Services Server certificate
- Secure Email (S/MIME) certificates
Our DNS resolvers will validate the signatures associated with your DNSSEC configuration and prevent issuance if the validation fails.
| The use of DNSSEC is NOT MANDATORY. You don’t need to configure DNSSEC for DigiCert to issue one of the certificates listed above. This information only applies to those using or planning to use DNSSEC. |
Items covered in this article
- Why is DigiCert doing this?
- What do I need to do to prepare for the new CA requirement to validate DNSSEC?
- Troubleshooting DNSSEC errors with your DNS Provider
- References
- Need help?
Why is DigiCert doing this?
DigiCert will start validating DNSSEC when verifying domain control and performing DNS CAA checks, in alignment with the CA/Browser Forum’s Ballot SC-085v2: Require Validation of DNSSEC (when present) for CAA and DCV Lookups. This ballot requires Certificate Authorities (CAs) to validate DNSSEC, if present, to verify domain control, pass CAA checks, and issue a certificate. Learn more about Ballot SC-085v2. With this ballot, CAs can no longer ignore misconfigured DNSSEC.
Benefits of DNSSEC
As stated in the Purpose of the Ballot, “DNSSEC adds an optional layer of security to DNS by enabling cryptographic validation of DNS resource records, ensuring that they are authentic and haven’t been tampered with…If a domain properly configures DNSSEC, DNSSEC validation can meaningfully reduce the risks associated with DNS spoofing or interception attacks against CAs [1]. Furthermore, DNSSEC validation by CAs provides options for domain owners to achieve provable security of the domain control validation process against network adversaries [1][2].”
What do I need to do to prepare for the new CA requirement to validate DNSSEC?
Identify DNSSEC configurations for your certificate domains before March 3, 2026. Then, what you need to do depends on whether you are using DNSSEC for these domains.
- I verified that we aren’t using DNSSEC for the domains in our certificates.
No action is required. - I verified that we use DNSSEC or plan to use it for the domains in our certificates.
If you’ve set up DNSSEC and it’s misconfigured, the DigiCert DNSSEC check may fail during domain control validation, and/or during the CAA check if you have CAA records for your domains. DNSSEC misconfiguration may prevent certificate issuance.
Verify DNSSEC configurations before March 3, 2026
To prevent DigiCert DNSSEC validation failures, DigiCert recommends using our tool to verify your DNSSEC is properly configured for domains you plan to use in certificate requests before March 3, 2026.
DigiCert DNSSEC Health tool: https://dnssec.health
When DigiCert starts validating DNSSEC on March 3, be prepared to troubleshoot if a broken DNSSEC configuration blocks certificate issuance.
Troubleshooting DNSSEC errors with your DNS Provider
The errors in this section are not DigiCert system-side errors. We provide them to help you troubleshoot DNSSEC errors with your own DNS provider, unless you use DigiCert's DNS services: UltraDNS or DigiCert DNS Essentials (formerly DNS Made Easy).
Preparing for March 3, 2026
As DigiCert prepares for the new requirement to validate DNSSEC during domain control validation and CAA record checks, we are monitoring DNSSEC validation failures. Currently, CAs do not need to act on failed checks. Starting March 3, DNSSEC validation failures will block domain validation and CAA checks, preventing certificate issuance.
Here are the most common reasons our DNSSEC check fails. This list is not exhaustive and may be updated.
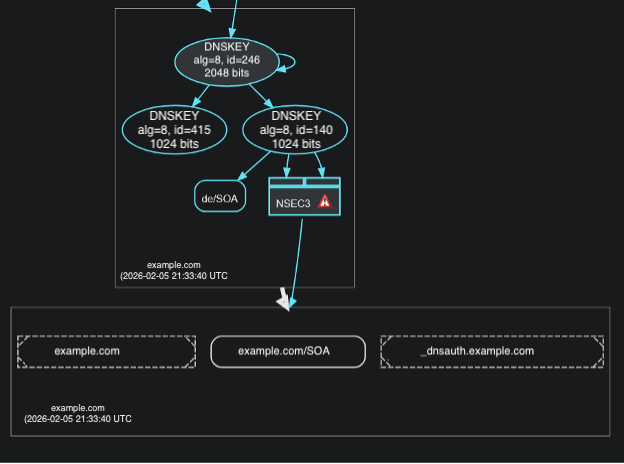
Next Secure (NSEC) Missing Error
Most common reasons for receiving this error:
- The domain is unsigned with the Domain Name System (DNS) provider, which prevents the creation of NSEC records.
- A problem with how NSEC records are generated or formatted in response to a query.
- For unexpected NSEC behavior, contact your Authoritative DNS provider.
Example
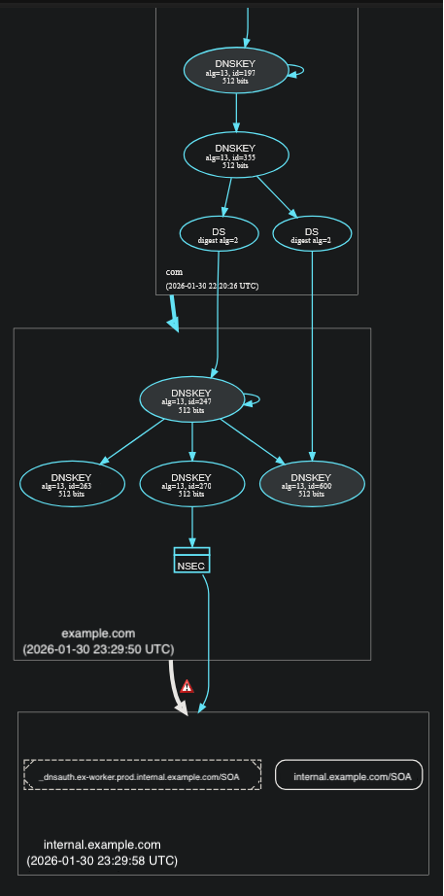
Resource Record Signatures (RRSIGS) Missing Error
Either the zone file or the specific record being validated is not signed.
- Some DNS providers require manual re-signing of zone files after records are created or edited. This can result in a signed domain with unsigned records, which fail to resolve when DNSSEC validation is enforced.
- An accompanying error message of "Could not establish validation of INSECURE status of unsigned response. Reason: No signed NSEC/NSEC3 records..." indicates an unsigned child domain (sub.domain.com) that exists outside of a signed parent (domain.com).
- Contact your DNS provider to resolve this issue. Additional DNS record configurations may be needed.
Example
References
- Ballot SC-085v2: Require Validation of DNSSEC (when present) for CAA and DCV Lookups
- Enable DNSSEC to Prevent Security Issues
Need help?
If you have questions or concerns, please contact your account manager or DigiCert Support.

