
Knowledge Base
Adding Exception to MS Defender, if its blocking DigiCert PKI Client application
Scenario
The UI components of the DigiCert PKI Client application are implemented by making use of Microsoft HTML Applications (HTA). These HTAs are standalone applications that get executed using the same models and technologies as Microsoft Internet Explorer, but outside of the browser. Microsoft Defender and a few other security providers are blocking the usage and launch of HTA-based applications.
There is a growing trend for attackers to more heavily utilize tools that already exist on a system rather than relying totally on their own custom malware.
Using HTA files or its partner in crime, mshta.exe is an alternative to using macro-enabled documents for attacks and has been around for a long time. It is a tool so flexible it even has its own attack technique documented under MITRE ATT&CK.
What makes HTA applications dangerous?
It is a signed, native Microsoft binary (mshta.exe) that already exists on Windows operating systems that can execute code in a variety of ways, and this makes it a prime application of interest since code execution can be proxied through it.
Mshta.exe can also be used to bypass application whitelisting defenses and browser security settings.
As such, in a few cases, it is observed that the end-user is not able to launch the DigiCert PKI Client as the PKI Client console application is based on Microsoft HTML application (HTA).
Solution
For an end-user machine with Admin rights
For customers experiencing blocking of HTA-based applications, in order to enable the smooth operation of DigiCert PKI Client, we recommend adding “exceptions” to your control settings to whitelist DigiCert PKI Client, by following the below steps:
- Go to Start > Settings > Update & Security > Windows Security > Virus & threat protection.
- Under Virus & threat protection settings, select Manage settings, and then under Exclusions, select Add or remove exclusions.
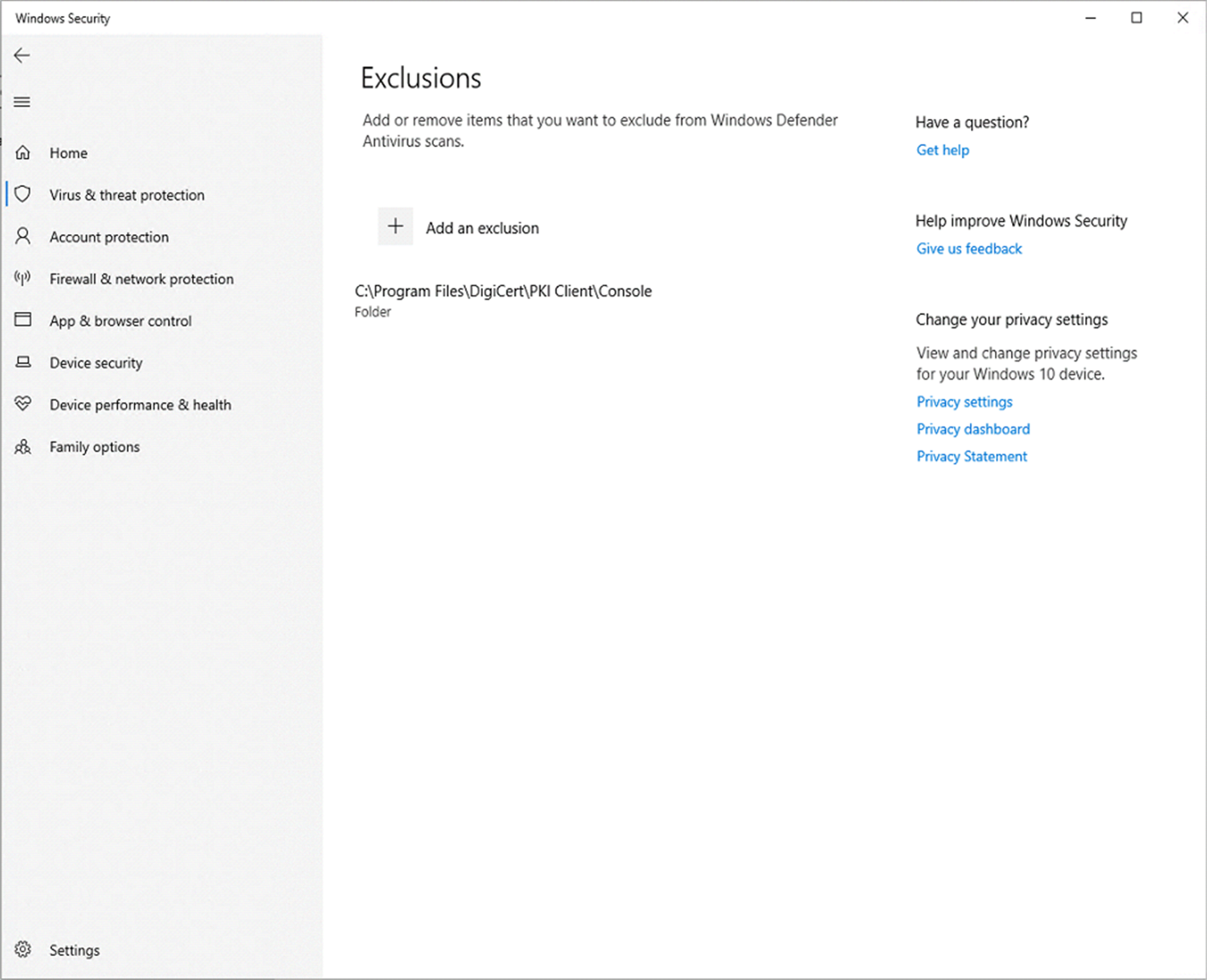
- Select Add an exclusion, and then select Folders from the drop-down list and navigate to PKI Client installation directory “C:\Program Files\DigiCert\PKI Client”, and from here select the folder ‘Console’. At this point, you would have to provide the Admin credentials, if the logged-in user does not have Admin privileges.
For Domains where MS Defender is configured through Group Policy Object (GPO)
- On your Group Policy management machine, open the Group Policy Management Console, right-click the Group Policy Object (GPO) defined for Microsoft Defender and click Edit.
- Open the Path Exclusions setting for editing, and update as below:
- Set the option to Enabled.
- Under the Options section, click Show....
- Specify directory “C:\Program Files\DigiCert\PKI Client\Console”, and Enter 0 in the Value column.
- Open a command prompt and execute the command ‘$ gpupdate /force’ to force the policy update

