
Knowledge Base
Migrate escrowed certificates from PKI Platform 7.x to 8.x
Step 1: PKI WS KMS installation and configuration
Follow the steps for Managed PKI Web Services Key Management Server Installation and Configuration Guide available for download from the Managed PKI Control Center.
Pre-requisites for setting up PKI WS KMS:
Use a Registration Authority (RA) certificate that is stored on a software-based Java keystore, not a Hardware Security Module (HSM).
PKI WS KMS must be configured on http:// rather than https://. Communications between enterprise client and the Key Management Server are secured using basic authentication.
Step 2 : Run key export tool
Please contact digicert representative to get access to the key export tool
For the steps and details about the export tool refer to the document
See: DigiCert PKI Platform - Key Export User Guide
- First, run the Key Export tool with a small set of data using the Common Name filter. "To export all certificates" use a blank value for the filter.
- Once the execution is completed, the console output will show the number of certificates imported successfully vs failed. Sample output:
**************************************************************************************************** TIME ELAPSED - 00:06:01 TOTAL CERTIFICATE COUNT - 99 TOTAL SUCCESS IN THIS RUN - 97 TOTAL FAILURES IN THIS RUN - 2 ---------------------------------------------------------------------------------------------------- Serial Number Reason ---------------------------------------------------------------------------------------------------- [0319f6117e9e20d873e20a59d9d2f7a7] - The Key Management Server could not find the key escrow record for this certificate serial number. Correct the request and try again. A707 [5f9bd6c5b0be0d923c2e53653695feee] - The Key Management Server could not find the key escrow record for this certificate serial number. Correct the request and try again. A707 **************************************************************************************************** 2021-06-04 03:23:20,889 [Thread-5] - [] - Terminating application 2021-06-04 03:23:20,894 [Thread-5] - [] - Completed producer thread. |
3. If any failures occur, check the contents of the log file named
mpki-export-utility.log. You can also manually check key recovery from the Control Center console. If required, rerun the tool to process only failed records.
4. Use zip files created at folder .\mpki-export-utility-tmp\final\ to import them into your Local Key Management Service.
Step 3: Import certificates to PKI Platform 8.x Local Key escrow and recovery service(LKMS)
- PKI Enterprise Gateway 1.21.1 or later is required for this feature to work.
- Please contact DigiCert representative to enable this feature on your 8.x account.
Import process will take considerably longer time to complete if the RA certificate is stored within the HSM. DigiCert strongly recommends the use of a software-based RA certificate, which can be downloaded from within the PKI Manager portal (main/parent account), under: Tasks -> Get an RA Certificate
Use the main account or sub-account where PKI Enterprise configuration is configured with Key escrow and recovery service.
For more details about Import feature, you can refer to PKI Enterprise Gateway Deployment Guide, under the section “Configuring PKI Enterprise Gateway for Non-DigiCert Key Import”
- Create a policy for certificate import. Manage certificates > Manage policies > Create a new policy
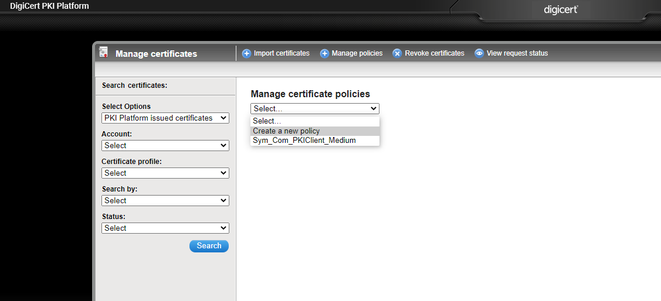
Select Key Store as Local for importing certificates to PKI Platform 8.x LKMS. Save the policy.
- Click on Import Certificate, select the policy created in step #1 and check “Select this option to access RA Agent to import certificates” and click on Continue.
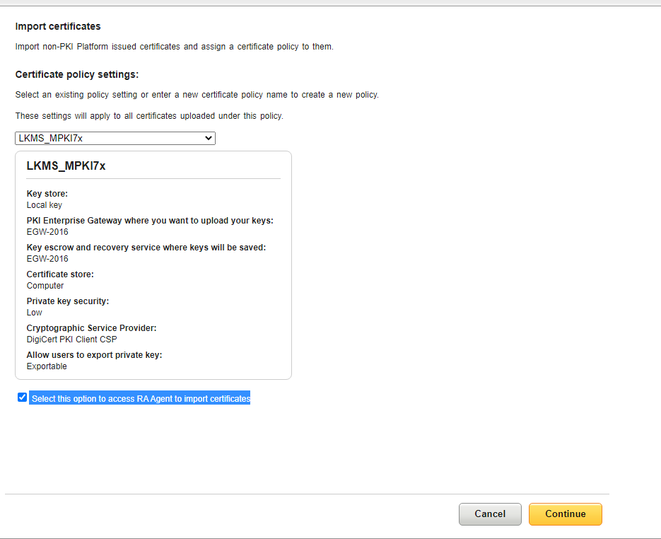
- On the next page, choose zip file created by export tool and click on “Submit and return to PKI Manager”.
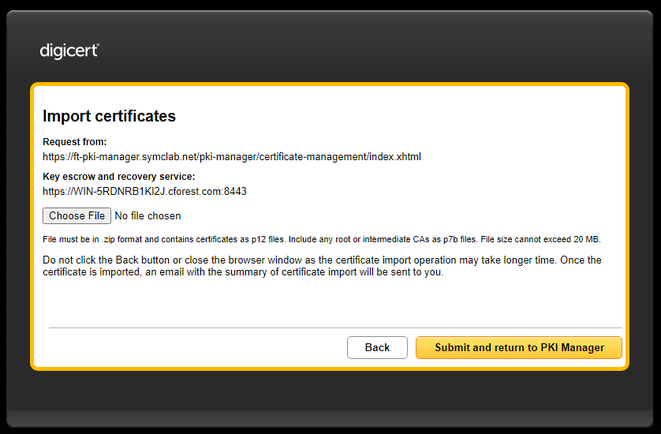
IMPORTANT NOTE: certificates and keys are imported directly into your LKMS system - DigiCert does not have access to any private keys since they are locally escrowed on your LKMS system.
- PKI Admin will receive an email when import is complete. Email will have the location of log file in LKMS server and also the status of import.
Sample email:
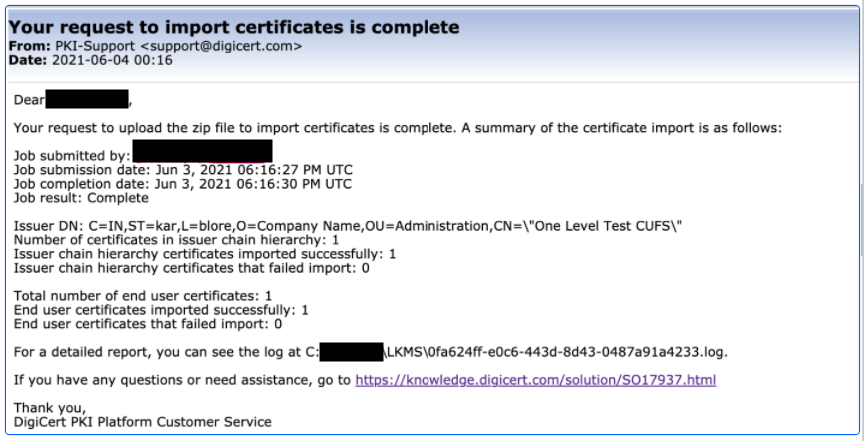
If multiple zip files are created by export tool, wait for the status complete mail for previous import before proceeding with the next zip file.
Step 5: Search imported certificates
- On Manage certificates, search for the imported certificate. Select Non-PKI Platform issued certificates from Select Options. Select the Account and Certificate policy.
Make sure the count of certificates matches the total number of certificates imported from your Managed PKI 7x account.
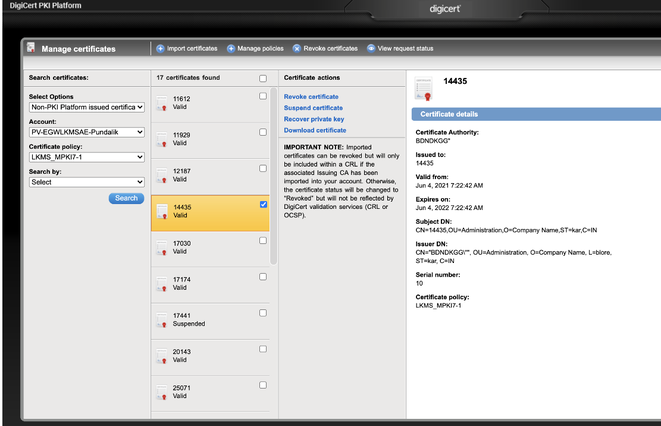
- Select a certificate to test the key recovery process. Only dual key recovery is supported through the PKI Manager admin console and via SOAP PKI Web Service API, where two different administrators, with the appropriate permissions, are required.
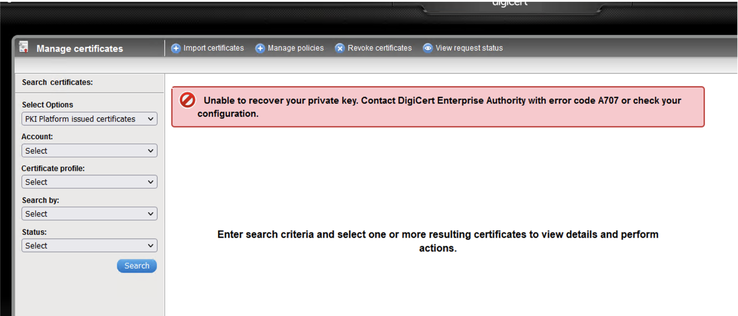
- From PKI Manager UI, when the first admin attempts a key recovery, the below error page will be displayed. Key recovery on the same certificate will complete successfully when using a different authorized admin.
-
IMPORTANT NOTES:
a) Imported certificates can be revoked but will be included within a CRL if associated Issuing CA has been imported into your account. Otherwise, certificate status will be changed to "Revoked" in the UI but will not be reflected by DigiCert validation services (CRL or OCSP).
b) You will only be able to perform all other certificate lifecycle operations (e.g. Suspend/Resume/Revoke) after July 12th 2021, provided the associated Issuing CA is available on your account.
- For searching certificates using SOAP PKI Web Service API, use “importedcert” as the profileOID value. Seatid and accountid search filters are not supported when searching imported certificates.
If you have any queries or concerns, please contact PKI Support.

