Knowledge Base
Transitioning public S/MIME certificate issuance from PKI Platform 8 to Trust Lifecycle Manager in DigiCert ONE
IMPORTANT: NEW TIME FOR END OF ISSUANCE End of issuance of public S/MIME (Secure Email) certificates will happen 6 hours earlier than originally communicated. DigiCert will now stop issuing public S/MIME (Secure Email) certificates from DigiCert® PKI Platform 8 on March 14, 2025, by 17:59:59 GMT/UTC. |
End of issuance of public S/MIME (Secure Email) certificates from DigiCert® PKI Platform 8 is scheduled for March 14, 2025, by 17:59:59 GMT/UTC. This includes certificates issued from profiles created from any of the following PKI Platform 8 public S/MIME certificate templates:
- Secure Email
- S/MIME (Digital Signature only)
- S/MIME (Digital Signature only) for Intune
- S/MIME (Encryption only)
- Secure Email Gateway
To continue issuing DigiCert public S/MIME certificates without interruption, you must transition your certificate issuance to DigiCert® Trust Lifecycle Manager in DigiCert ONE as soon as possible.
| Below are general steps for transitioning public S/MIME certificate issuance from your current PKI Platform 8 account to a Trust Lifecycle Manager account, to be completed with a dedicated DigiCert transition team at your earliest convenience. Contact your account manager to begin the transition process. If you don't know who your account manager is, email pki_sales@digicert.com. |
Steps for transitioning public S/MIME certificate issuance from PKI Platform 8 to Trust Lifecycle Manager in DigiCert ONE:
1. Ensure that your PKI Platform 8 contact information (Organizational Contact, Technical Contact, etc.) is up-to-date. If you need to update it, start here.
2. Gather the required information about your PKI Platform 8 issuing CA(s):
- Full name
- Expiration date
- Serial number
3. Gather required information about all active PKI Platform 8 public S/MIME certificate profiles:
- Name of each profile
- Name of CA connected to each profile
- Name of template from which each profile was created:
- Secure Email
- S/MIME (Digital Signature only)
- S/MIME (Digital Signature only) for Intune
- S/MIME (Encryption only)
- Secure Email Gateway
- Number of valid certificates currently issued from each profile
4. Set up a test account (if needed), in the region that you specify, in a separate DigiCert ONE transition environment.
DigiCert ONE test accounts are:
|
5. Set up a DigiCert CertCentral account. (If you already have a CertCentral account, no action is required.)
Why do you need a CertCentral account to issue public S/MIME certificates from Trust Lifecycle Manager in DigiCert ONE? Public S/MIME certificates issued from Trust Lifecycle Manager in DigiCert ONE chain to a shared ICA certificate in CertCentral. This shared ICA certificate is fully compliant with new regulations guiding the issuance of public S/MIME certificates. |
6. Integrate your Trust Lifecycle Manager account with your CertCentral account by adding the DigiCert CertCentral connector.
7. Submit your Organization Name for public SMIME validation (required to issue a certificate).
8. Create new public S/MIME certificate profiles in DigiCert ONE.
Important: When creating new S/MIME profiles from any of the above S/MIME-related templates, you should select the new ICA certificate, which is fully compliant with new S/MIME baseline requirements. See Secure Email (S/MIME) ICA Certificate Replacements to identify which new ICA certificate is right for you. |
- Intune-specific profiles -
Are you using public S/MIME certificate profiles configured from the S/MIME (Digital Signature only) for Intune template?
After DigiCert has migrated your profiles to a new compliant Public S/MIME Issuing CA, you must create new trusted profiles on the Microsoft Intune portal. Follow the steps under the Intune Trusted Certificate profile section in the Intune integration guide to create the trusted profiles for the new Issuing CA chain.
- Microsoft Autoenrollment profiles -
Are you using public S/MIME certificate profiles configured with the Microsoft Autoenrollment enrollment method?
After DigiCert migrates your Microsoft Autoenrollment-enabled profiles to a new compliant Public S/MIME Issuing CA, the “Autoenrollment configuration file” gets updated, and you need to follow the steps below:
- In the PKI manager portal, download the updated "Autoenrollment configuration file". Then, import the configuration file into Autoenrollment Configuration Utility onto the AE Server.
For more details, see the "DigiCert® PKI Enterprise Gateway - Autoenrollment Server Deployment Guide" knowledge base article - DigiCert PKI Platform Autoenrollment Server deployment guide.
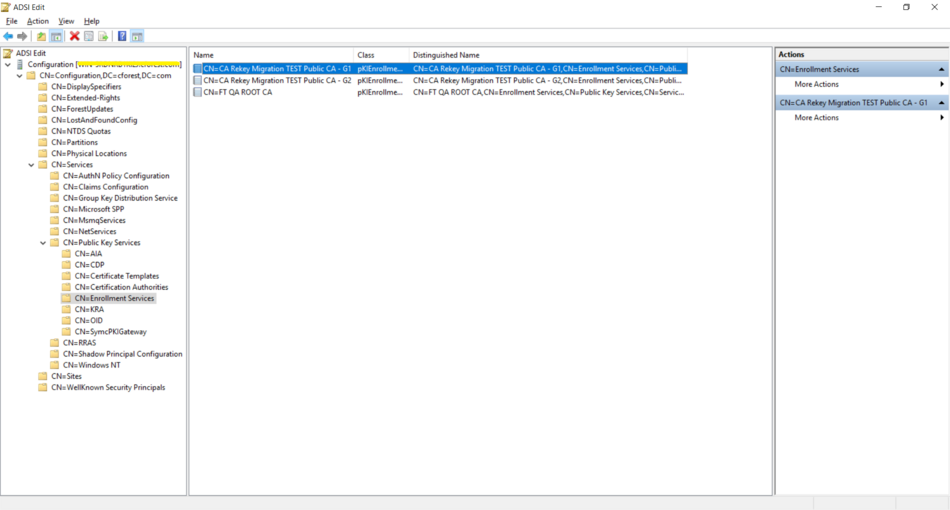
- After all the profiles associated with the old ICA certificate are migrated, delete the old ICA certificate from "Enrollment Services" using the "ADSI Edit" tool. See the screenshot below.
- In the PKI manager portal, go to Enrollment Services.
- Select the ICA certificate you must delete, then select Action > Delete.
- In the PKI manager portal, download the updated "Autoenrollment configuration file". Then, import the configuration file into Autoenrollment Configuration Utility onto the AE Server.